Note: activities in this section require a Windows host computer with a trusted platform module installed.
What is a trusted platform module?
A trusted platform module or TPM is a co-processor that can be a discrete device but is more commonly integrated into other devices like the CPU. The TPM performs two main functions: it stores private encryption keys, and it performs cryptographic functions often with those keys. The private keys cannot be read by the host system, so a hacker cannot steal the keys through something like a memory dump. A TPM is similar to a YubiKey or PIV card, except that it is built directly into a computer’s hardware. Thus, the computer can authenticate itself to do things like decrypt the hard drive automatically on boot.
Here’s an oversimplified explanation of how a trusted platform module can authenticate a system:
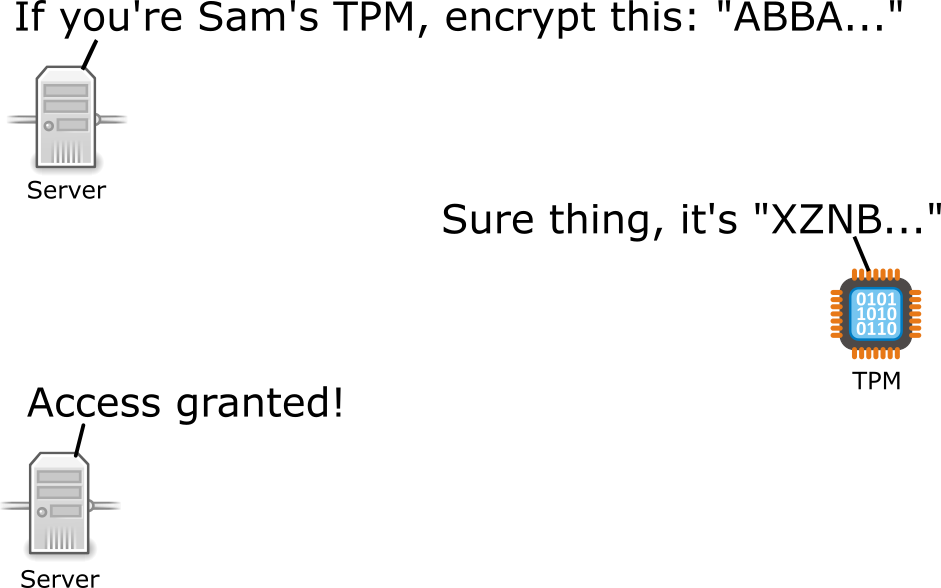
Windows uses a TPM to perform encryption (eg. bitlocker), enterprise authentication, and key/certificate storage — all without the need for user passwords or interaction. For example, Windows can use a TPM to automatically unlock a bitlocker encrypted drive at boot time.
How to check to see if you have a trusted platform module
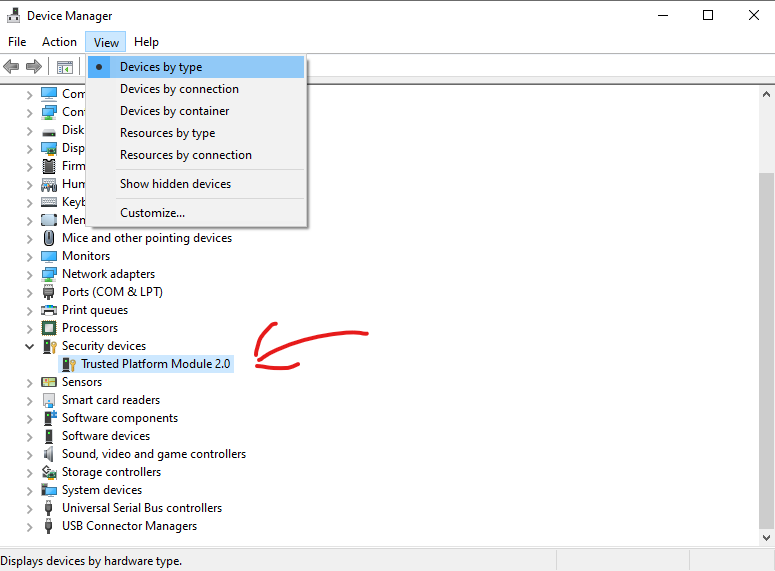
Method 1: The device manger:
Run devmgmt.msc to open the device manager. Make sure that you are viewing by device type. Scroll down to “Security Devices.” You should see a trusted platform module listed if it is installed.
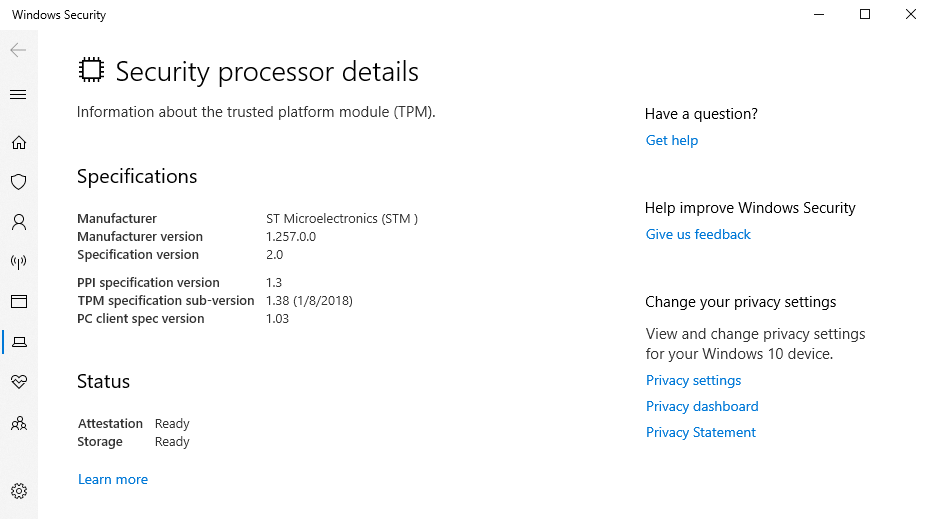
Method 2: The settings app:
Open the Windows Settings app and search for the “Security Processor” section. Go to that section to view details of your TPM.
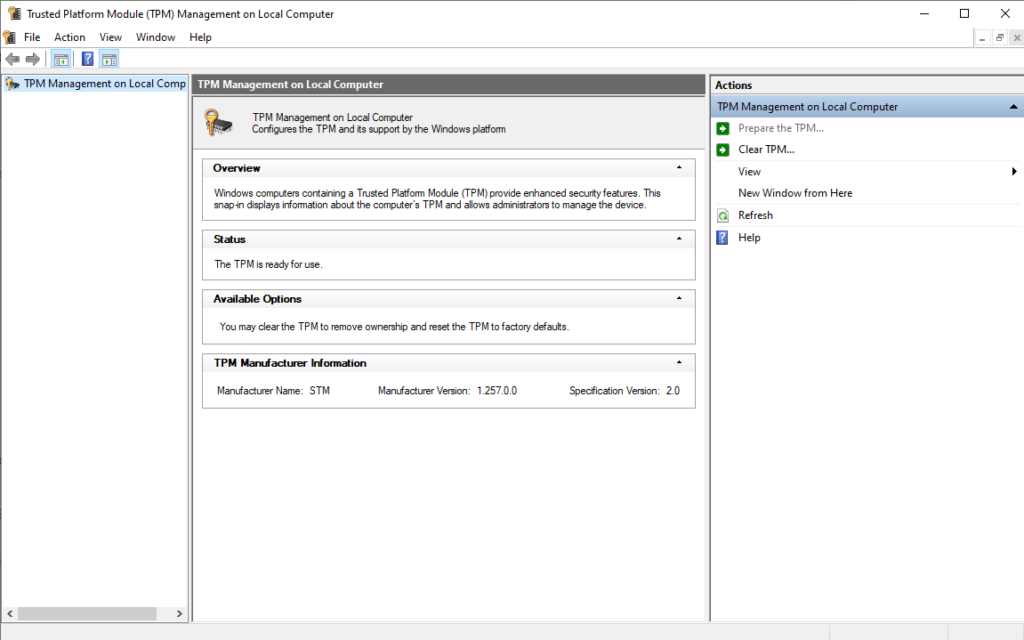
Method 3: The TPM management console:
The TPM management console is no longer under active development. However, it is still distributed with Windows. To open the TPM management console, run tpm.msc. Details of the system’s TPM are listed as well as an option to clear the TPM to the right. Clearing the TPM will erase all private keys and perhaps make your device unable to boot if the TPM is required to unlock the drive.
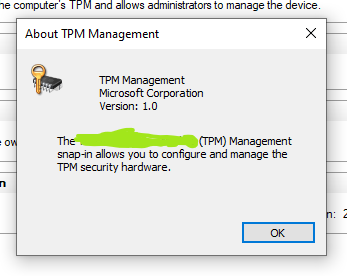
Flag 1
Open tpm.msc. Go to Help ->About TPM Management in the menu bar. The flag is the text covered by the green blob.
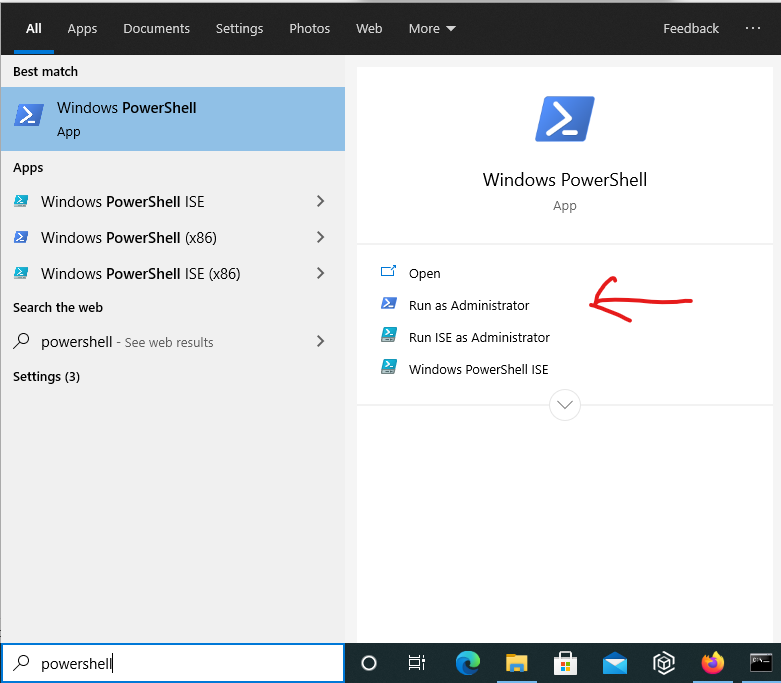
Powershell and trusted platform modules
Powershell is one of the better ways to interact with a system’s trusted platform module. Interaction with the TPM requires elevated privileges. So run powershell as Administrator by right clicking on its icon on the start menu and selecting, “Run as administrator.”
Now run the following command in powershell:
Get-Tpm
This will list basic information about the installed trusted platform module.
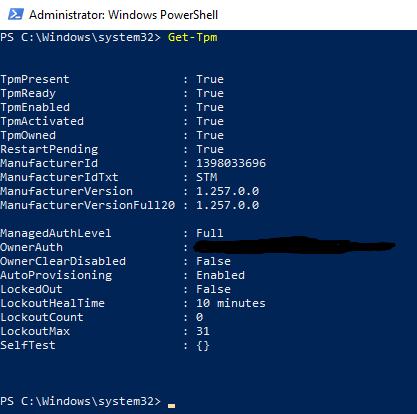
The “OwnerAuth” value contains password data for unlocking the device if the TPM locks itself when it suspects someone has been tampering with the device. You can create a new owner auth value based on a password to unlock the device using the ConvertTo-TpmOwnerAuth command. The Set-TpmOwnerAuth will set the TPM’s owner auth value, and Unblock-Tpm will unlock the device using the owner auth value set. In addition, the Import-TpmOwnerAuth will import the owner auth value into the Windows registry.
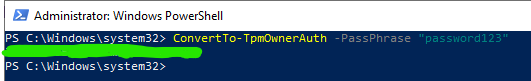
Flag 2
Use the ConvertTo-TpmOwnerAuth command to convert the password, “password123”, to a TPM authorization value. The flag is the TPM authorization value.
Powershell and getting the TPM endorsement key
Every TPM has an endorsement key injected by the manufacturer. The endorsement key can identify the chip and register it with an organization’s certificate authority. We can use Powershell to get information about the endorsement key. Run the following command:
Get-TpmEndorsementKeyInfo -Hash "Sha256"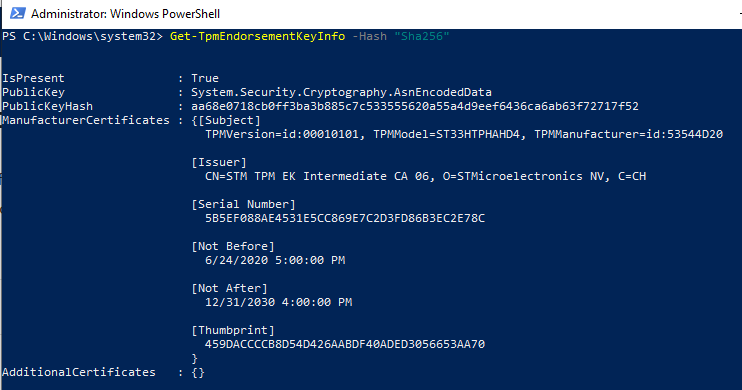
A user can view the TPM’s endorsement public key, hash, and certificate. The private key exists on the TPM module and cannot be retrieved. An administrator can use the public key and certificate to establish trust with the TPM the same way public keys and certificates establish trust over the web using TLS. An attacker would find it difficult to replicate the TPM module since the private key never touches the host machine.
Flag 3
Enter the following command into Powershell:
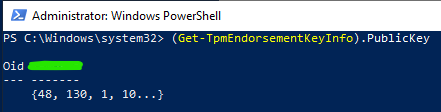
(Get-TpmEndorsementKeyInfo).PublicKeyThe flag is under the green marking. Feel free to try to extract the full public endorsement key from your TPM at this point for personal gratification and glory.
Additional References
- Powershell Documentation for Trusted Platform Modules: https://docs.microsoft.com/en-us/powershell/module/trustedplatformmodule/?view=windowsserver2019-ps
- Microsoft Documentation for Trusted Platform Modules: https://docs.microsoft.com/en-us/previous-versions/windows/it-pro/windows-8.1-and-8/jj131725(v=ws.11)
- Trusted Computing Group (TPM): https://trustedcomputinggroup.org/resource/trusted-platform-module-tpm-summary/
